To combat malware effectively, analyzing network traffic is essential. By examining how malware communicates across networks, cybersecurity teams can uncover its origins, understand its methods, and see the scope of the threat. Here’s a look at five key tools that simplify and enhance network traffic analysis for malware in 2025.
Packet Analyzer
Packet analyzers, or “packet sniffers,” capture and inspect data packets traveling across the network. They allow you to examine all incoming and outgoing data from a potentially infected system, providing insights into how malware interacts with command-and-control (C2) servers, exfiltrates data, or spreads. For instance, you can trace outgoing packets to spot any stolen information, like credentials or cookies. Tools like ANY.RUN’s sandbox include features that make it easy to view data exchanges for specific connections, giving you a clear picture of malware behavior through color-coded sent and received packets.
Suricata IDS
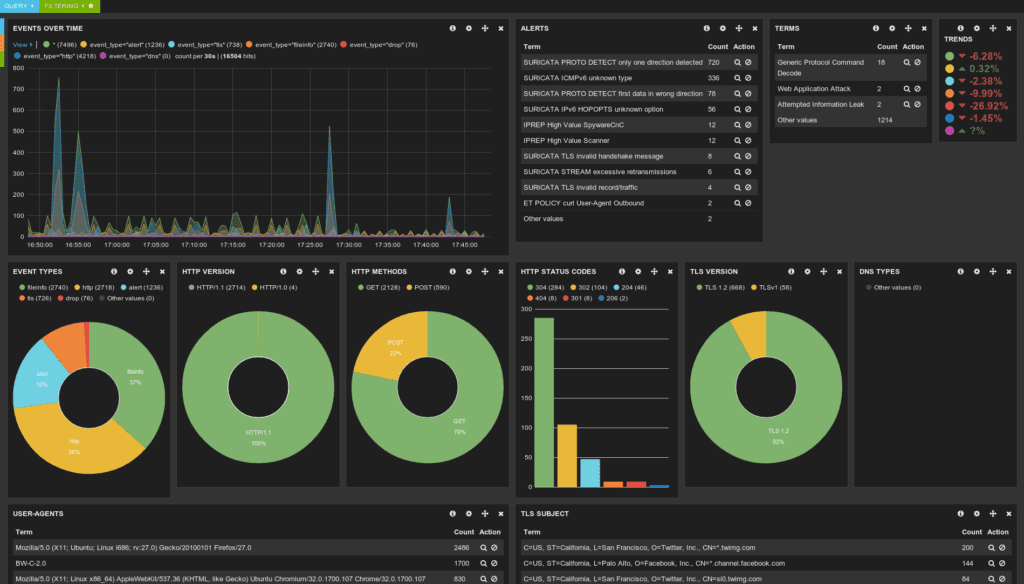
Suricata, an open-source intrusion detection system (IDS), is built for real-time network monitoring, intrusion prevention, and packet capture. It analyzes traffic for known attack patterns and flags suspicious activity instantly. ANY.RUN integrates Suricata to help users detect threats quickly by analyzing packet and flow data against a set of rules. Suricata’s alerts provide valuable insights into unusual connections or payloads, helping analysts respond faster to threats.
MITM Proxy
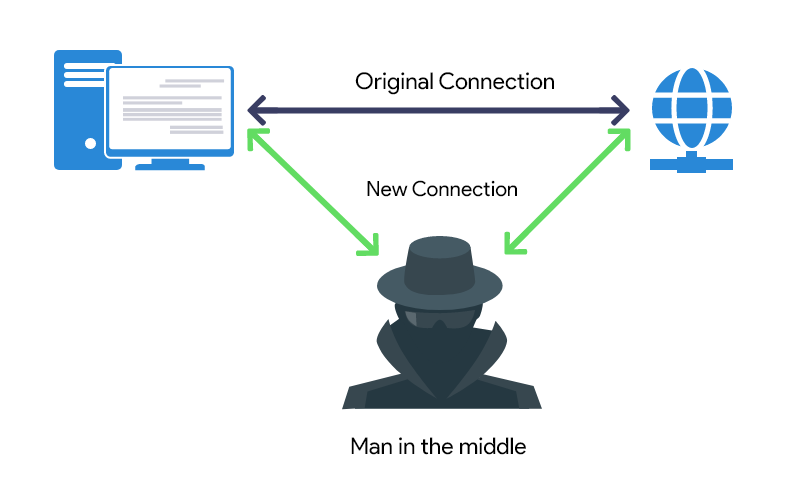
A Man-in-the-Middle (MITM) Proxy is essential for decrypting encrypted malware traffic. By positioning itself between malware and its C2 servers, it intercepts and decrypts HTTPS communications, making it possible to view sensitive data like IP addresses, URLs, or stolen credentials. ANY.RUN’s sandbox, for instance, offers a MITM Proxy feature that lets analysts view decrypted traffic in an organized interface, enabling detailed inspections of communication flows. In cases of data theft, such as malware exfiltrating data to a Telegram bot, the MITM Proxy can reveal key details like bot tokens and chat IDs.
PCAP Extractor
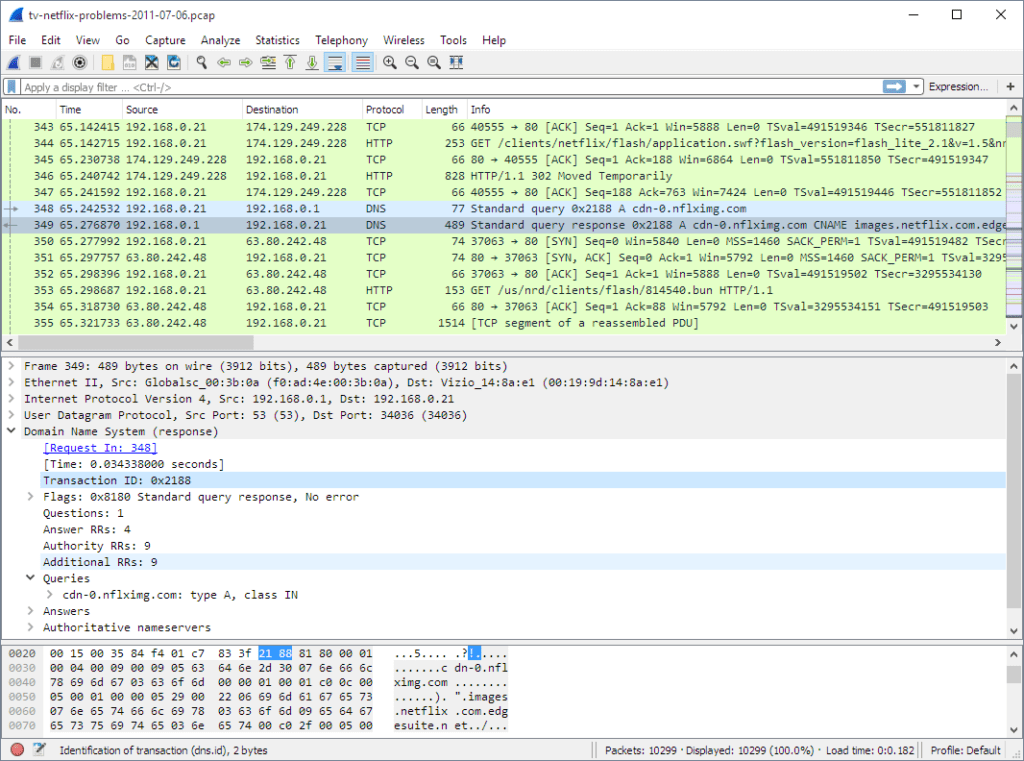
A PCAP (Packet Capture) Extractor allows analysts to capture and save network traffic during a malware session in PCAP files. These files, which contain packet-level data, can be reviewed offline or analyzed further with other tools. ANY.RUN’s integrated PCAP Extractor captures all relevant network interactions, from HTTP requests to DNS queries, giving analysts a way to revisit session data in detail.
Wireshark
One of the most popular network analysis tools, Wireshark captures and saves network traffic data in PCAP format. It provides in-depth analysis options and supports extensive protocol examination, making it a top choice for malware analysis.
tcpdump
tcpdump is a command-line packet analyzer that captures packets and saves them in PCAP format. Lightweight and versatile, it’s widely used for quick captures and works well in scripts for automated network analysis.
NetworkMiner
NetworkMiner is a passive network traffic analysis tool that extracts files and metadata from PCAP files. It’s especially useful for forensic analysis, helping users reconstruct and analyze malware-related network activity.
Malware Sandbox
A malware sandbox creates an isolated environment to safely observe malware behavior. Many modern sandboxes combine various tools—packet analyzers, MITM proxies, IDS, and PCAP extractors—into one platform, providing an all-in-one solution for malware analysis. ANY.RUN, for instance, lets users examine all network connections, HTTP and DNS requests, and associate these with specific processes during execution. This consolidated view helps teams understand malware’s interactions, simplifying detection and response.
ANY.RUN

ANY.RUN is an interactive malware sandbox that provides real-time analysis with visual representations of network traffic, processes, and system activity. It supports various integrations, including Suricata IDS, to aid in network traffic inspection.
Cuckoo Sandbox

Cuckoo is an open-source sandbox that automates malware analysis by running files in isolated virtual environments. It supports custom configurations, making it a flexible solution for dynamic analysis.
VirusTotal Sandbox
VirusTotal offers a sandbox feature that allows users to analyze files in a safe environment and view the results across multiple antivirus engines. It’s widely used for its accessibility and integration with VirusTotal’s large database of malware samples.
These tools are indispensable for analyzing malware’s network behavior, giving analysts insights into communication patterns and exfiltration methods. Platforms like ANY.RUN combine these tools, providing a streamlined way to analyze the full scope of a threat and respond effectively.

Founder of ToolsLib, Designer, Web and Cybersecurity Expert.
Passionate about software development and crafting elegant, user-friendly designs.
Stay Updated with ToolsLib! 🚀
Join our community to receive the latest cybersecurity tips, software updates, and exclusive insights straight to your inbox!