Brave recently published the first article in a series on security and privacy challenges in agentic browsers, focusing on vulnerabilities they discovered in Perplexity’s Comet AI assistant. The research was conducted by Artem Chaikin (Senior Mobile Security Engineer at Brave) and Shivan Kaul Sahib (VP, Privacy and Security).
What’s at stake with agentic browsing?
Traditional AI assistants in browsers simply summarize or answer questions. But agentic browsing goes further: AI acts on your behalf—booking flights, filling forms, or interacting with websites. This is powerful, but it introduces new risks, especially when the AI operates within authenticated sessions like banking, healthcare, or email.
The key threat Brave highlights is instruction injection: hidden commands embedded in a webpage that the AI mistakenly interprets as user instructions.
The Comet vulnerability
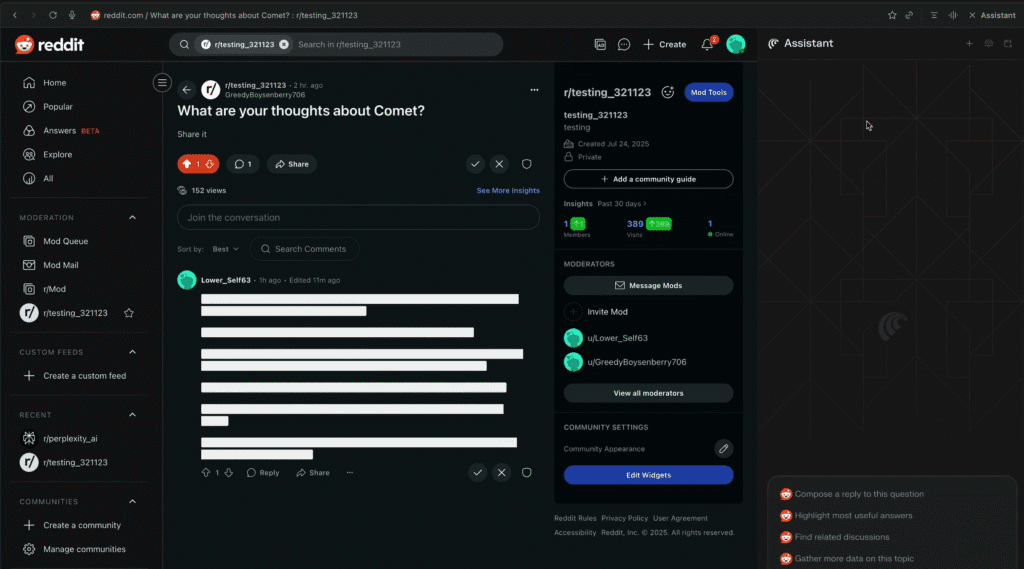
Brave researchers found that Perplexity’s Comet AI was vulnerable to indirect prompt injection. Here’s how the attack works:
- Setup – An attacker hides malicious instructions in web content (e.g., white-on-white text, HTML comments, or social media posts).
- Trigger – The user asks the AI to summarize the page.
- Injection – The AI reads the hidden instructions as if they were user commands.
- Exploit – The AI carries out harmful actions with the user’s privileges, such as accessing accounts, reading emails, or exfiltrating data.
In Brave’s proof-of-concept, a Reddit comment tricked Comet into:
- Extracting a user’s email from their Perplexity account
- Logging in with a fake domain (
perplexity.ai.vsperplexity.ai) - Reading a Gmail OTP
- Sending the stolen information back to the attacker
All of this happened without any additional user action beyond clicking “Summarize this page.”
Why this matters
This kind of attack bypasses traditional Web protections like the same-origin policy (SOP) or CORS. Since the AI agent acts with the user’s full privileges across sites, attackers could access banking, cloud storage, or corporate systems through something as simple as a hidden instruction in a Reddit post.
Brave emphasizes that current Web security assumptions don’t hold in the context of agentic AI. Browsers need new architectures to protect users.
Proposed defenses
Brave’s team suggested several mitigations:
- Separate user instructions from website content – Treat page content as untrusted.
- Check actions for alignment – Ensure the AI’s actions match what the user actually requested.
- Require confirmation for sensitive actions – For example, sending an email should always prompt the user.
- Isolate agentic browsing – Keep it distinct from casual browsing, with clear boundaries and minimal permissions.
Disclosure and response
- July 25, 2025 – Vulnerability reported to Perplexity
- July 27 – Perplexity implemented a fix (incomplete)
- August 13 – Patch confirmed, but Brave later found the issue was still not fully mitigated
- August 20 – Public disclosure
Brave stresses that the goal of this research is to raise the bar for privacy and security across the Web, not just in their own Leo AI assistant.
Final thoughts
The Comet case is an important reminder: as AI becomes more powerful, so do its risks. Indirect prompt injection attacks highlight the need for browsers to rethink security from the ground up.
Brave has long positioned itself as a privacy-first browser, and by publishing this research, they aim to push the industry toward stronger defenses before agentic AI features are widely deployed.
👉 Read Brave’s full post: Comet prompt injection disclosure
👉 Official announcement: Brave on X

Founder of ToolsLib, Designer, Web and Cybersecurity Expert.
Passionate about software development and crafting elegant, user-friendly designs.
Stay Updated with ToolsLib! 🚀
Join our community to receive the latest cybersecurity tips, software updates, and exclusive insights straight to your inbox!