In a recent analysis of a 1% sample of GitHub repositories, AquaSec uncovered a startling reality: approximately 37,000 of these repositories are vulnerable to RepoJacking, a hacking technique exploiting repository renaming. This threat extends even to tech giants like Google and Lyft.
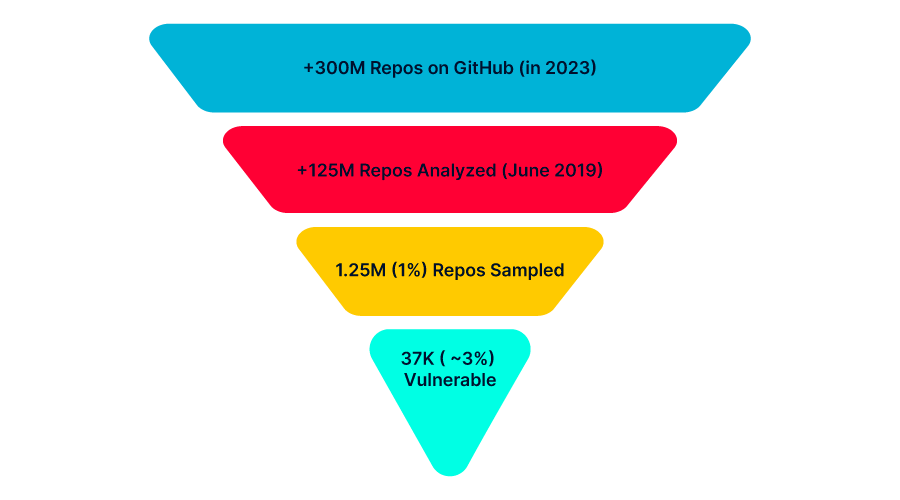
AquaSec’s methodology involved scrutinizing 1.25 million GitHub repositories to identify vulnerabilities to RepoJacking. They found that nearly 3% of repositories were affected, including those owned by major corporations. Utilizing tools like GHTorrent provided a comprehensive view of these vulnerabilities.
The real-world risks of exploitation are evident, as seen in cases involving Google and Lyft. AquaSec identified construction instructions in a Google readme file pointing to a GitHub repository belonging to a company acquired by Google, potentially exposing users to malicious code injection. Similarly, a Lyft installation script fetching a ZIP archive from a vulnerable repository poses a risk of malicious code execution.
Businesses are advised to regularly check their GitHub repositories for any links fetching resources from external repositories. It’s crucial for companies to retain their previous company names as placeholders to prevent attackers from hijacking them. This vigilance is essential as many other organizations could also be affected by this threat.
In conclusion, AquaSec’s analysis reveals an alarming extent of vulnerability to RepoJacking, affecting GitHub repositories of all sizes, including those of major corporations. This discovery underscores the crucial importance of continuous monitoring of GitHub repositories and the implementation of proactive measures to prevent repository hacking attacks.
AquaSec blog post: https://www.aquasec.com/blog/github-dataset-research-reveals-millions-potentially-vulnerable-to-repojacking/

Founder of ToolsLib, Designer, Web and Cybersecurity Expert.
Passionate about software development and crafting elegant, user-friendly designs.
Stay Updated with ToolsLib! 🚀
Join our community to receive the latest cybersecurity tips, software updates, and exclusive insights straight to your inbox!