Chinese AI startup DeepSeek, which has recently gained widespread attention for its DeepSeek-R1 reasoning model, suffered a major security lapse that left a ClickHouse database publicly accessible online. The breach exposed over a million log lines, including chat history, API keys, backend service details, and sensitive metadata, raising serious concerns about the company’s security practices.
Unrestricted Database Access and Critical Risks
Security researchers from Wiz discovered that DeepSeek’s database, hosted at oauth2callback.deepseek.com:9000 and dev.deepseek.com:9000, was left unprotected, allowing unauthenticated users to execute arbitrary SQL queries. This level of access meant that attackers could potentially:
- Retrieve chat logs and plaintext API secrets
- Extract internal files and sensitive backend information
- Escalate privileges and execute malicious commands
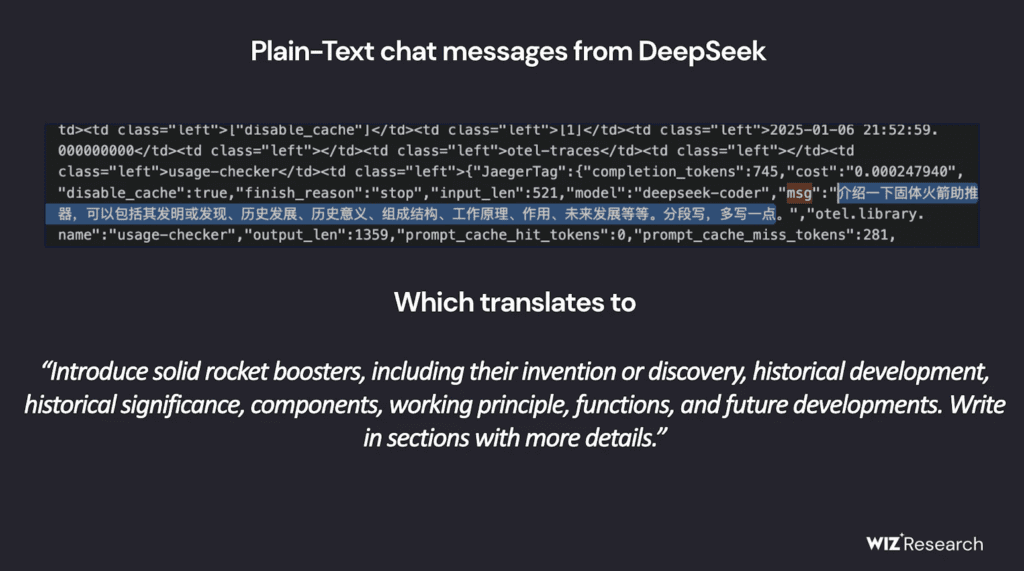
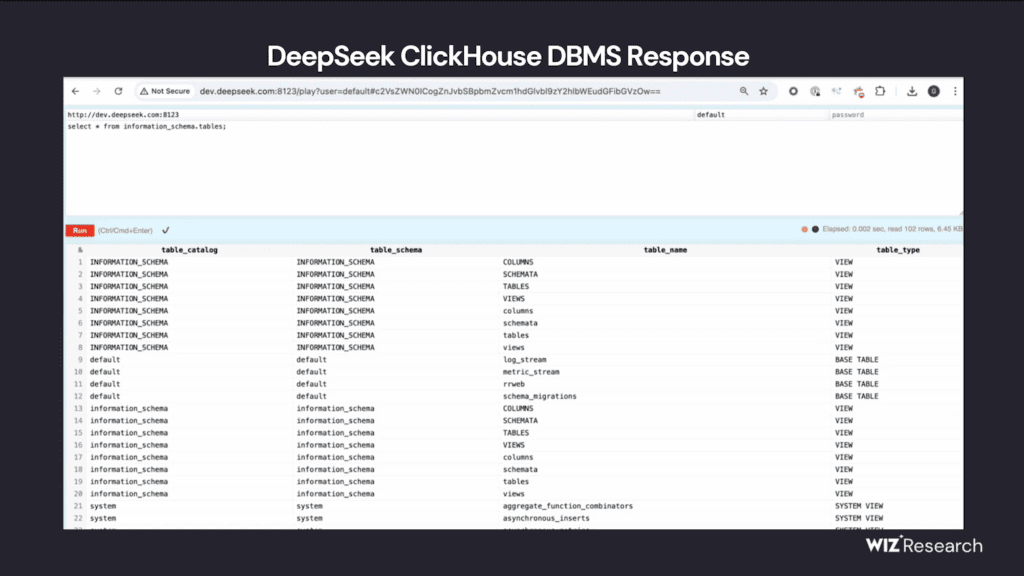
The breach underscores how rushing to deploy AI services without proper security measures can expose sensitive infrastructure.
How the Leak Was Discovered
Researchers mapped DeepSeek’s external attack surface, identifying around 30 subdomains. While most were routine chatbot interfaces and documentation pages, further investigation uncovered two open ClickHouse database ports (8123 and 9000).
ClickHouse, a popular real-time analytics database, allows direct HTTP-based SQL query execution. Wiz researchers accessed the /play endpoint and listed database tables, revealing a log_stream table containing highly sensitive data, including plaintext logs of user conversations and API credentials.
“An attacker with access to this database could retrieve plaintext passwords, sensitive server data, and proprietary AI information,” Wiz Research reported.
DeepSeek’s Response and Growing Scrutiny
Upon being notified, DeepSeek quickly secured the exposed database but has not yet provided an official statement. The incident comes at a sensitive time for the company, as it faces increasing scrutiny:
- Privacy Concerns: Italy’s data protection regulator blocked DeepSeek’s apps, requesting details about its data handling practices. Ireland’s Data Protection Commission has also sent inquiries.
- Ties to China: DeepSeek’s Chinese origins have raised national security concerns in the U.S.
- Plagiarism Allegations: Reports suggest OpenAI and Microsoft are investigating whether DeepSeek used OpenAI’s API to train its models, a method known as distillation.
A Wake-Up Call for AI Security
This breach highlights the real-world risks of AI security, not just futuristic concerns like adversarial attacks. Failing to secure AI infrastructure can lead to serious data leaks, privacy violations, and national security risks.
“As organizations race to adopt AI, security frameworks are often overlooked,” Wiz Research stated. “This incident serves as a wake-up call for the entire industry.”

Founder of ToolsLib, Designer, Web and Cybersecurity Expert.
Passionate about software development and crafting elegant, user-friendly designs.
Stay Updated with ToolsLib! 🚀
Join our community to receive the latest cybersecurity tips, software updates, and exclusive insights straight to your inbox!